
Section 3: Network Reconnaissance
U.S. Army Cyber School
Version Date: 1 JAN 2022
Skills and Objectives
-
SKILL CCNE005: Network Information Gathering ¹ ²
-
CCNE005.001 Identify items of interest when performing internal/external reconnaissance ¹ ²
-
CCNE005.002 Describe passive methods used for network reconnaissance ¹ ²
-
CCNE005.003 Describe active methods used for network reconnaissance ¹ ²
-
-
SKILL CCNE006 Network collection devices and relevant data ¹ ²
-
CCNE006.001 Identify sources of network data collection ¹
-
CCNE006.002 Explain network data collection devices and placement ²
-
-
SKILL CCNE007: Active Network Reconnaissance and Analysis ¹ ²
-
CCNE007.001 Discuss best practices for network scanning and enumeration ¹ ²
-
CCNE007.002 Describe the use of scanning tools and methods ¹ ²
-
CCNE007.003 Perform real-time network scanning ²
-
CCNE007.004 Perform analysis of network scanning results ²
-
-
SKILL CCNE008: Network Forensics ¹ ²
-
CCNE08.001 Map a network through correlation of relevant network artifacts gathered through reconnaissance and analysis ²
-
| CONTENT | TIME |
|---|---|
Facilitation: Passive Network Information Gathering |
20 minutes |
Facilitation: Passive External Network Reconnaissance |
25 minutes |
Break |
15 minutes |
Facilitation: Active External Network Reconnaissance and Analysis |
25 minutes |
Demo: Performing Scans and Analyzing Results |
20 minutes |
Break |
15 minutes |
Facilitation: Passive Internal Network Reconnaissance |
30 minutes |
Demo: Passive Internal Network Reconnaissance |
30 minutes |
Lunch |
90 minutes |
Facilitation: Network Artifact Correlation |
30 minutes |
Demo : Audit configuration files with NIPPER |
15 minutes |
Break |
15 minutes |
Activity: Donovian Mapping & Reconnaissance (DMR) |
150 minutes |
| Section Totals: | |
|---|---|
Section 3 Allotted days |
1.0 Days |
Section 3 Allotted Break Time (includes lunch): |
135 minutes |
Section 3 Activity Timeline Total: |
150 minutes |
Section 3 Facilitation and Demo Timeline Total: |
195 minutes |
Section 3 Timeline Total: |
480 minutes |
Outcome: This section re-enforces skills related objectives 5-8.
-
Understand and perform passive network information gathering through open source intelligence and host configuration analysis
-
Understand and perform active network recon and enumeration
-
Understand what information is important to collect to create a network map
Section Introduction:
As a defender it is important to know what systems, OS’s, and services are on that network along with normal communication patterns.
As an attacker, discovery of systems and services is crucial to formulating a plan of attack. An attacker spends 90 percent of their time performing reconnaissance and 10 percent of their time performing an actual attack.
There are two general approaches to Network Reconnaissance.
Active:
-
Active scanning is the process of transmitting packets to a remote host and analyzing corresponding replies to locate and identify devices
Passive:
-
On the offensive side, the client listens for beacons and other traffic sent periodically by a target. On the defensive side, passive scanning can be done using an IDS, it watches the network and look for irregular traffic or other indicators of compromise. A passive scan generally takes more time, since the client must listen and wait for traffic versus actively probing
Internal:
-
From inside your network, an internal vulnerability scan operates inside your networks* Key Loggers firewall to identify real and potential vulnerabilities inside your network
External:
-
From outside your network, looks for holes in your network firewall, where malicious outsiders can break in and attack your network.
Uses and practices for network scanning
Network scanning is obviously a critical part of reconnaissance, as it allows you to take a look into the hardware structure and software capabilities of a target. One of the main goals is to discern the vulnerabilities of your target, whether it be an adversary or your own organization. Scanning can be approached in several different manners, but here we will focus on it categorically.
Scanning Nature:
-
Active - this method aims to provide a comprehensive report of possible open or closed ports at the time of the scan. Active scanning typically performs very fast, and can contain options to vary that speed. However, it is flawed when attempting to detect ports that are filtered by firewalls. A well known disadvantage of active scanning is that it is very intrusive. Active probes typically solicit a response that would not have been sent otherwise. This traffic is more likely to be detected and logged by the host. In this methodology, packets (whether legal or illegal combinations) will be sent to a target, hence "active". The "stealth" strategies discussed later are still considered active by this definition. in this section we will focus on active scanning.
-
Passive - identifies network services by observing traffic generated by servers and hosts as it passes an observation point. Distinctively, passive scanning has an advantage of being non-intrusive. In fact, it generally cannot be detected without in-depth and purposeful investigation. Due to the obscure nature of passive scanning, it can be ran long-term to better detect active services running on transient hosts such as machines that are frequently powered off or hosts temporarily disconnected from the network. Passive scanning can also detect services that active scanning may miss due to firewall configurations. In this methodology, the service acts more as a sniffer and no "hard" packet is sent out.
External |
Internal |
|
Passive |
* DNS Lookups (DIG) |
* Packet Sniffing |
Active |
* Ping scans |
* DNS Queries |

Identify items of interest when performing passive External Reconnaissance
Passive host and service discovery is much less straight forward and requires more time than active discovery methods, but it carries less risk of discovery by administrators and NSM (IPS/IDS). Passive approaches require knowledge of particular systems, their nuances, and how they generate network traffic. In general, the passive reconnaissance approach can be categorized as attempted gathering of information about a target network or host without direct interaction.
Network owners must understand what information can be gleaned from their network traffic and have a full understanding of their network footprint. Information can be gathered from a target passively by eavesdropping on a target using tools such as Wireshark, tcpdump, and tshark.
Passive External Network Reconnaissance: Information Gathering
Performing Passive Reconnaissance commonly involves identifying the following:
-
IP Addresses and Sub-domains - usually one of the first steps in passive reconnaissance, it’s important to identify the net ranges and sub-domains associated with your target(s) as this will help scope the remainder of your activities.
-
Use passive tools to collect the target’s owned IP address blocks
-
IANA or one of their IRR’s
-
-
Collect all the DNS domain and sub-domain names.
-
Fierce - is an IP and DNS recon tool is written in PERL, famous for helping IT sec professionals to find target IPs associated with domain names.
-
Unicornscan - is one of the top intel-gathering tools for security research. It has also a built-in correlation engine that aims to be efficient, flexible and scalable at the same time.
-
Trace the IP route to the target using:
-
Traceroute (using TCP, UDP or ICMP)
-
open Visual Trace
-
VisualRoute.com
-
-
-
Identifying External/3rd Party sites
-
Companies that support or collaborate with your target
-
Target’s competitors
-
Look-up Org charts from CogMap
-
-
-
Identifying People - Identifying names, email addresses, phone numbers, and other personal information can be valuable for pretexting, phishing or other social engineering activities. Use open-source to collect information on subject browse social media sites:
-
Company website (example: www.ccboe.net)
-
Third-party data repositories (companies that host data for your targeted organization)
-
Tools such as:
-
Maltego (provides the ability to lookup email addresses based on a given domain. ) wiki
-
Recon-ng - already built in the Kali Linux distribution and is another great tool used to perform quickly and thoroughly reconnaissance on remote targets.
-
theHarvester - is another great alternative to fetch valuable information about any subdomain names, virtual hosts, open ports and email address of any company/website.
-
Jigsaw - is used to gather information about any company employees. This tool works perfectly for companies like Google, Linkedin, or Microsoft, where we can just pick up one of their domain names (like google.com), and then gather all their employee’s emails on the different company departments.
-
SpiderFoot is one of the best reconnaissance tools out there if you want to automate OSINT and have fast results for reconnaissance, threat intelligence, and perimeter monitoring.
-
Creepy is a geo-location OSINT tool for infosec professionals. It offers the ability to get full geolocation data from any individuals by querying social networking platforms like Twitter, Flickr, Facebook, etc.
-
-
Message boards
-
User Forums
-
Search Engines
-
google
-
yahoo
-
duckduckgo
-
-
Social Media:
-
Facebook
-
Twitter
-
LinkedIn
-
-
Job Portals (To find job titles):
-
Monster
-
Linkedin
-
Glass Door
-
-
Document and File Metadata Tools:
-
Whois records
-
Email Tracking (Hidden Images, Link Redirection) - who is checking emails
-
YesWare
-
HubSpot
-
BananaTag
-
GetNotify
-
ReadNotify
-
WhoReadMe
-
MsgTag
-
DidTheyReadIt
-
Social Engineering Toolkit (SET)
-
-
Other people "look-up" pages:
-
-
Identifying Technologies - Identifying the types and versions of the systems and software applications in use by an organization is an important precursor to identifying potential vulnerabilities. You can ID technologies from many sources including:
-
File extensions ( https://www.computerhope.com/issues/ch001789.htm )
-
Server responses
-
Job postings/interviews
-
LinkedIn
-
GlassDoor
-
-
Directory listings on Target Webpage
-
Login splash pages
-
Website content
-
X-Powered-By
-
Wappalyzer determines technology as you browse the website
-
-
Content-Types
-
Server Software and Version
-
Cookie Information
-
Builtwith - a cool way to detect which technologies are used on any website on the internet.
-
Tools:
-
wget
-
HTTrack
-
Pavu
-
WebRipper 2.0 (www.calluna-software.com)
-
WinWSD
-
DomainPunch
-
WebExtractor
-
-
-
Public acquisition records
-
Shodan.io
-
Spyse - is another OSINT search engine that lets anyone grab critical information about any website in the world. Quite simply, Spyse is an infosec crawler that gets useful information for red and blue teams during the reconnaissance process.
-
Document Searches
-
Google Hacking - Database
-
System fingerprinting tools:
-
Ettercap – passive TCP/IP stack fingerprinting.
-
NetworkMiner – passive DHCP and TCP/IP stack fingerprinting (combines p0f, Ettercap and Satori databases)
-
Nmap – comprehensive active stack fingerprinting. nmap -O 192.168.0.20
-
p0f – comprehensive passive TCP/IP stack fingerprinting.
-
NetSleuth – free passive fingerprinting and analysis tool
-
PacketFence – open source NAC with passive DHCP fingerprinting.
-
PRADS – Passive Real-time Asset Detection System. Passive comprehensive TCP/IP stack fingerprinting and service detection
-
Satori – passive CDP, DHCP, ICMP, HPSP, HTTP, TCP/IP and other stack fingerprinting.
-
SinFP – single-port active/passive fingerprinting.
-
XProbe2 – active TCP/IP stack fingerprinting.
-
Device Fingerprint Website - Displays the passive TCP SYN fingerprint of your browser’s computer (or intermediate proxy)
-
queso - well-known tool from the late 1990s which is no longer being updated for modern operating systems
-
-
-
Identifying Content of Interest - Identifying web and email portals, log files, backup or archived files, or sensitive information contained within HTML comments or client-side scripts is important for vulnerability discovery and future penetration testing activities.
-
Site content can reveal potential access points (e.g. web portals), sensitive data (login credentials), and more. As you browse the site be on the lookout for the following:
-
Externally facing web portals, webmail, and administrative consoles
-
Test pages
-
Log files
-
Backup files
-
Configuration files
-
Database dump files
-
Client-side code
-
/etc/passwd and /etc/shadow or SAM database
-
-
-
Identifying Vulnerabilities - it’s possible to identify critical vulnerabilities that can be exploited with further active penetration testing activities solely by examining publicly available information
-
Vulnerability Focus:
-
Network
-
OS
-
Applications
-
Service
-
Configuration Errors
-
-
OS Fingerprinting
-
Nmap -PO -sV 10.1.0.3
-
-PO - Ping scan
-
-sV - Probe open ports to determine service/version info
-
-
Ettercap ( https://www.ettercap-project.org/ )
-
-
The following are some of the methods you might use to identify vulnerabilities:
-
Researching known software vulnerabilities based on identified technologies
-
Examining URLs - the url may indicate what is used to host webpage.
-
.aspx may mean SharePoint
-
ASP.NET may indicate a Microsoft IIS
-
-
Passive scanning via an intercepting proxy
-
Shrink-wrap code - an act of exploiting holes in unpatched or poorly configured software.
-
Reviewing error messages
-
ICMP
-
HTTP(s) status codes ( https://en.wikipedia.org/wiki/List_of_HTTP_status_codes )
-
-
-
Tools:
-
Saint (https://www.carson-saint.com/products/saint-security-suite/vulnerability-management/)
-
Linux or Mac
-
Identifies Vulnerabilities on:
-
Network devices
-
Operation systems
-
Desktop Apps
-
Web Apps
-
Databases
-
-
-
Nessus ( https://www.tenable.com/ )
-
Linux, Windows and Mac
-
Malware/Botnet detection
-
-
GFI LanGuard ( https://www.gfi.com )
-
Patch Management
-
Vulnerability Assesment
-
Network Auditing
-
Change Management
-
Inventory Management
-
-
Shadow Security Scanner ( https://www.safety-lab.com )
-
Core Impact ( https://coresecurity.com )
-
Qualys ( https://qualys.com )
-
OvenVAS ( https://openvas.org )
-
Retina CS ( https://eeye.com )
-
NextPost ( https://rapid7.com )
-
Wapiti ( https://wapiti.sourceforge.io/ )
-
-
Vulnerability databases
-
NIST: ( https://nvd.nist.gov/ )
-
CVE: ( https://www.cvedetails.com/ )
-
Rapid 7: ( https://www.rapid7.com/db/?type=nexpose )
-
Mitre Vulnerability Database: ( https://cve.mitre.org/ )
-
-
Compliance Auditing:
-
PCI DSS - Payment Card Industry Data Security Standard (PCI DSS) compliance is designed to protect businesses and their customers against payment card theft and fraud. If your business accepts, stores, or transmits card data, PCI DSS compliance validation is required by card brands such as Visa, MasterCard and Discover.
-
NERC - The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) exists to improve the reliability of the critical bulk power SCADA systems that create and transport electricity around the continent, and the goal of a NERC compliance program is to ensure that the bulk electric system in North America is reliable, adequate and secure. It’s not enough to just plan for natural disasters or accidents-the bulk power system now must be planned, designed, built and operated in a manner that also takes into account modern threats to security, including attacks from cyber criminals. NERC compliance programs are required to help prevent these attacks.
-
FISMA - The Federal Information Security Management Act (FISMA) requires Federal agencies to develop, document, and implement an information security program to safeguard their systems and data. In addition to government agencies, FISMA also applies to contractors and third parties that use or operate an information system on behalf of a Federal agency.
-
SOX - Sarbanes-Oxley Act (SOX) requires that publicly-traded companies ensure their internal business processes are properly monitored and managed. Financial reporting processes are driven by IT systems, so IT needs to be configured securely and maintained properly. The Securities and Exchange Commission (SEC) has identified five areas that need to be addressed to meet SOX internal control requirements and support SOX compliance, two of which are risk assessment and monitoring.
-
GLBA - The Gramm-Leach-Bliley Act is a U.S. federal law created to control how financial institutions deal with a consumer’s non-public personal information (NPI). This is information that a financial institution collects when providing a financial product or service that can identify an individual and that isn’t otherwise publicly available.
-
The Act has three main elements:
-
The Privacy Rule, which regulates the collection and use of NPI
-
The Safeguards Rule, which requires financial institutions to implement a security program to protect NPI
-
Pretexting provisions, which prohibits access to NPI under false pretense
-
-
-
HIPAA - The Health Insurance Portability and Accountability Act (HIPAA) protects the privacy and security of personal health information (PHI). Any healthcare organization that stores, processes, or transmits PHI must meet HIPAA compliance requirements, including any business associates that perform functions or provide services on their behalf.
-
GDPR - The General Data Protection Regulation (GDPR compliance) protects the personal data of EU citizens regardless of the geographical location of the organization or the data. Organizations around the world must be compliant with GDPR by 25th May 2018. Changes to people, processes, and technology are required to ensure that personal data is correctly controlled, processed, maintained, retained, and secured. Penalties for infringement of the General Data Protection Regulation can be up to €20,000,000 or 4% of worldwide annual turnover, whichever is the greater amount.
-
CIS Benchmarks - The Center of Internet Security (CIS) is a non-for-profit organization that develops their own Configuration Policy Benchmarks, or CIS benchmarks, that allow organizations to improve their security and compliance programs and posture. This initiative aims to create community developed security configuration baselines, or CIS benchmarks, for IT and Security products that are commonly found throughout organizations.
-
SCAP - The Security Content Automation Protocol (SCAP) is a method that uses open standards to organize and express security-related information. It’s not a regulation or a mandate, but it allows federal agencies to automate a great deal of manual processes and make data standardization and comparisons a lot easier.
-
FDCC - The Federal Desktop Core Configuration (FDCC compliance) is an older federal standard that defines a standardized desktop configuration to improve security. Although FDCC benchmarks have been superseded by USGCB benchmarks in 2010 and 2011, many agencies are still working on their FDCC compliance. If you’re one of them, we can help you achieve FDCC compliance.
-
USGCB - The United States Government Configuration Baseline (USGCB) is a United States government-wide initiative that guides federal agencies on what they can do to improve and maintain effective configuration settings focusing primarily on security. This initiative aims to create security configuration baselines for IT and security products, specifically on desktops and laptops, deployed across federal agencies. While it’s not a standalone regulation like FISMA, USGCB compliance is a core requirement of FISMA.
-
-
Possible tools for gathering:
* WHOIS queries
* Job Site listings
* Phone numbers
* Google searches
* Passive OS Fingerprinting
Describe passive methods used for external network reconnaissance
Before deep diving into identification of vulnerabilities, gathering data to properly scope recon activities must be performed. It wouldn’t make much sense to spend a lot of time looking for Microsoft IIS web server related vulnerabilities when the target you are after runs Apache for their web servers. This can be performed in multiple ways.
OP Notes Demo
Passive External Network Reconnaissance: DNS
DNS is critical to the operation of the Internet for resolving hostnames to IP addresses. Therefore, DNS servers contain vast amounts of data that can be used to gain information.
-
RFC 3912
TCP-based transaction-oriented query/response protocol that is widely used to provide information services to Internet users. While originally used to provide "white pages" services and information about registered domain names, current deployments cover a much broader range of information services. The protocol delivers its content in a human-readable format. -
The WHOIS lookup helps determine where the site is hosted, who owns the IP block, and may list organizational contacts that may be useful for social engineering.
-
Most whois queries will return false information as most people opt for privacy of their domain information in order to protect against email harvesting, spam, and social engineering attempts on the administrative contact.
instructor@net1:~$ whois ccboe.net

Using ccboe.net as the example, identify answers to the questions below:
What does ccboe stand for?
Columbia County Board of Education
Who is the DNS registrar?
Network Solutions, LLC
When does the domain registration expire?
June 30, 2021
How many Name Servers are their?
2, NS1.CL.BELLSOUTH.NET, NS2.CL.BELLSOUTH.NET
Woo is the administrator?
James Van Meter
What is the administrator’s email address?
hostmaster@ccboe.net
What is the administrator’s phone number?
1-706-541-2721
Where is the location of the technology department possibly located?
6430 Pollards Pond Road, Appling, GA 30802
Google Maps Link
-
It quickly becomes apparent that if not sanitized properly, a multitude of information can be gleaned from the whois query. Occasionally, net range is displayed with a CIDR and could prove useful for future DNS reverse lookups.
Should this be avoided and if so, how?
Register the domain with anonymous registration services under a pseudonym. Often times domain name registrars will offer whois privacy (also known as domain privacy) as a service that in turn replaces the user’s information in the WHOIS with information of the forwarding service aka proxy of the registrar.
How might these be used as an defense tool?
If your system is being scanned or attacked you can use a WHOIS to possibly begin determining where the source of the malicious traffic is coming from.
Passive External Network Reconnaissance: DIG
Dig is a tool that returns key DNS information and can be used to supplement the query for specific records.
instructor@net1:~$ dig ccboe.net instructor@net1:~$ dig ccboe.net MX instructor@net1:~$ dig ccboe.net SOA instructor@net1:~$ dig ccboe.net TXT


Identify answers to the questions below:
Who is the SOA?
What type of mail server is listed?
Outlook
-
This method can be further enhanced with tools such as dnsrecon that will brute-force with a word-list to find hidden sub-domains using words such as sales, training, admin, etc. This method is considered semi-active, generating logs for unlisted sub-domains would look quite suspicious.
Passive External Network Reconnaissance: Zone Transfers
A zone transfer is typical between primary and secondary DNS servers to update records on a domain. This information, if allowed to be transferred externally through misconfiguration allows hostnames, IP’s, and IP blocks to be discovered. With this information, targets can be determined and information for possible social engineering.
Conduct a zone transfer using the following syntax:
instructor@net1:~$ dig axfr @nsztm1.digi.ninja zonetransfer.me

This zone transfer includes tons of information, the website will guide you along and you may format questions based on what you see.
What sub-domains have been found?
What mail servers are being used?
Can you determine location with the LOC file?
Passive External Network Reconnaissance: Host History
Using the website to conduct recon:
When was the domain first registered?
1996
When was the domain first registered?
-
netcraft.com can also be used to find extra information about a url, including the netblock owners and hosting history. The date first seen is December 1996 for "www.ccboe.net". Combine this with sites such as the wayback machine and see what you can come up with.
The key takeaway is that the traffic generated looks like normal DNS queries and the target is none the wiser that they are being probed for information. For further non attribution, use a third party web-site such as dns stuff or central ops to perform the queries.
Passive External Network Reconnaissance: Google Searches
Passive External Network Reconnaissance: Shodan
Use this site to conduct recon:

-
Shodan searches can reveal clues about technologies that are exposed with simple searches such as cam, phone, printer, Cisco. It is also useful for exposing remote access services, improperly configured services such as SMB, and network infrastructure.
-
Once an item of interest is selected, you can obtain copious amounts of information such as open services, banners, location, and applicable CVE vulnerabilities.
Active External Network Reconnaissance: Network Scanning
-
Remote to Local - refers to a remote host, outside the boundary of a specific network, performing some sort of scan on hosts internal to an enterprise network. This is one of the most commonly used pen-testing or attack methods likely to come from unknown external adversaries.
-
Local to Remote - occurs when a host, within the administrative control of an enterprise network, scans systems outside the network boundary. This strategy may cause serious legal issues against an enterprise network without the appropriate permissions since its infrastructure could be used for malicious purposes against Internet systems.
-
Local to Local - refers to a host that scans systems within the boundaries of an enterprise in which it resides. Local to local scanning activity can occur within or between network subnets and is normally employed by network/security admins per policy.
-
Remote to Remote - does not depend on certain boundaries. It mainly refers to world wide scanning campaigns. Rather than focusing on a specific network as a target, it aims at probing and exploiting the Internet’s services vices. This strategy is often distributed, possesses sophisticated stealth capabilities and is typically highly coordinated.
Scanning Approach:
-
Aim
-
Wide range target scan - typically little human interaction involved (auto-rooters, automated to scan a network for vulnerable machines)
-
Target specific scan - focused scanning of a predetermined target host or network (botnet scanning or low and slow scan)
-
-
Method
-
Single Source Scan - operates from a one to many fashion
-
Distributed Scan - multiple systems in a union to scan a network or host of interest
-
-
Ensure that you identify and explain the "STEALTH" scans… why stealth (what makes them stealthy?)
-
add when and why you would use the scans if possible (why and when to use UDP)
Active External Network Reconnaissance: Host Discovery
Local Area Network/Neighbor Discovery
Neighbor Discovery emulates ARP or IPv6 neighbor discovery by sending discovery packets for every usable address on the network. Although this is standard behavior, it should be used with a delay and hosts should not be queried sequentially. ARPing is an application for emulating ARP, and Ndisc6 is for emulating IPv6 neighbor discovery. Neither application is typically installed on any system by default.
-
Broadcast Ping and Ping Sweep
A broadcast ping sends an ICMP echo request to the network broadcast address. Send one ICMP packet that every host receives and all active hosts should respond. Most systems no longer respond to a broadcast ping
Ping sweep sends an ICMP echo request to every usable address on a network. This is effective if there are no firewalls, but it is very noisy. If used, there should be a delay between pings, and hosts pinged should not be sequential. Keep in mind that many modern OS’s like Windows 7 drop an ICMP Echo Request by default for security reasons. A ping sweep in IPv6 is infeasible because there are too many addresses in a typical /64 network.
fping -g -a 10.1.0.0/24
nmap –sn 10.0.0.0/24 (was -sP which is now deprecated)
for i in {1..254}; do ping -c 1 -W 1 10.1.1.$i | grep 'from'; done
-
ARP Scan
sudo arp-scan --interface=eth0 --localnet sudo arp-scan --interface=eth0 10.1.0.0/24 arping –c 1 –i eth0 172.16.32.2 (can only scan a single host, results vary) for ip in $(sew 1 254) ; do if ping -c 1 10.1.0.$ip>/dev/null; then echo "10.1.0.$ip UP"; fi ;done nmap –PR 172.16.32.2(legitimate scan that often does not show results) nmap -PR -6 fe80::f816:3eff:fed9:5116/64(takes a long time to run)
Active External Network Reconnaissance: Service Discovery (Port Scanning)
Service Discovery sends TCP or UDP packets to hosts on specific ports. This method queries which hosts are up and which sockets are bound. Because it is most likely that multiple packets are sent to multiple hosts, these techniques are very noticeable on the network unless a large amount of time (low and slow) is taken while completing these scans. For purposes intended to avoid detection, "stealth scans" can be employed. These techniques attempt to avoid filtering devices by using alternative sets of flag combinations to appear as legitimate traffic.
The most common methods of port scanning are SYN scans and TCP Full Connect Scans, with the first considered to be stealth. Other types of stealth scans will be explored in this section.
-
SYN Scan
SYN scan sends only one TCP packet with the SYN flag set to each destination port and waits for a SYN/ACK or RST. This is also known as a Stealth Scan. This method reports if there is an application listening on the target port and does not register on the host system, because no ACK is sent to the target. This method does not retrieve any information about the service.
nmap –sS 172.16.32.2 hping3 172.16.32.2 -S -V -p 443
-
Full Connect Scan
Full-Connect scan establishes a complete TCP three-way handshake with a system. The advantage of this method is that a fully functional connection to the target host is made which allows information to be gathered from the listening service (aka banner grabbing). The down side to this method is that the connection is logged on the system being targeted. If done many times, a netstat on that system shows many established connections between the source and target.
nmap –sT –sV 10.16.32.23 (Full TCP connect, service versioning) nmap –sT 172.16.32.2
-
Null Scan
A null scan has no flags set and a sequence number of 0. All legitimate traffic has flags set, causing any null scan traffic to stand out if viewed. This scan is useful to penetrate firewalls and routers set to filter certain flags out since it uses no flags. Open and filtered ports should have no response, filtered ports may also send an ICMP unreachable message, and closed ports should send a RST packet.
nmap -sN 10.50.1.1 hping3 -c 1 -V -p 80 -s 5050 -Y 10.50.1.1
-
FIN Scan
A fin scan is a packet with just the FIN flag set. The packet tries to close a connection that does not exist as a way to obtain information. Like the null scan it works to go through firewalls and routers, in addition to being considered stealthier due to the illegal flag combination. Open and filtered ports should have no response, filtered ports may also send an ICMP unreachable message, and closed ports should send a RST packet.
nmap -sF 25.50.75.100 hping3 -c 1 -V -p 80 -s 5050 -F 25.50.75.100
-
XMAS Tree Scan
A christmas tree scan is a packet with varying definitions. From nmap it is defined as a packet with FIN, PSH, and URG flags set, while ISS(IBM Internet Security Systems) defines it as all flags are set. Open and filtered ports should have no response, filtered ports may also send an ICMP unreachable message, and closed ports should send a RST packet.
nmap -sX 7.92.5.19 hping3 -c 1 -V -p 80 -s 5050 -M 0 -UPF 7.92.5.19
-
UDP Scan
A UDP Scan can be used to find *nix hosts that are blocking TCP and ICMP traffic. Since UDP is a stateless protocol it is often used to get through stateful firewalls. This kind of scan is not very useful for service discovery because UDP is connection-less. UDP is dependent on the application as to how or if there is a response.
nmap –sU -v 10.10.100.3
-
Idle Scan
An idle scan is a more complex stealth technique that utilizes the previously discussed SYN|ACK scan and the Half-Open scan. The scan aims to gather port information using a zombie station on the network where the scanning process appears to have been initiated by the zombie IP address instead of the actual source station who will spoof this address later in the process. This scanning method exploits IP fragmentation identification sequences and implements IP address spoofing.
nmap -sI 10.10.5.6 25.23.4.7
-
Window Scan
A window scan functions like an ACK scan but uses the windows size of the responses to determine whether it is open or closed. An ACK scan returns most results as filtered and can be fairly inaccurate. By using the window size the scan can better determine if it is open, closed, or filtered. If the window field is non zero it will display as open, a zero window field will display as closed, and either no response or ICMP unreachable will display as filtered.
nmap -sW 10.66.35.10
-
RPC scan
A RPC scan is looking for services that use RPC(remote Procedure Call). RPC allows for remote commands to be run on machines and this scan will determine the services and version of the service when run. In updated versions of nmap -sR is aliased to -sV (version scanning) and activates version scanning with the RPC scanning.
nmap -sR 10.50.22.29
-
FTP bounce scan
A FTP bounce scan uses an intermediate ftp server to send files to a third party to determine open ports. This scan requires an anonymous login.
nmap -b 10.1.1.3 10.2.5.1
-
Decoy scan
A decoy scan sends multiple packets to each ports with different source addresses. This makes it difficult to detect the source but generates lot of traffic. Using ME in your IP list specifies where it is used in the order, and with larger amounts of IPs can mean that yours will not display.
nmap -D 1.2.3.4, 5.6.7.8,ME 100.200.10.20
-
OS fingerprinting scan
An OS fingerprinting scan uses TCP/IP stack fingerprinting to determine what OS is being used. By sending TCP and UDP packets it gathers information such as window size TCP option ordering, and IP ID sampling and runs that information against its OS database. If a match is found it provides Vendor, OS, Generation, and device type.
nmap -O 6.2.9.5
-
Version scan
A version scan uses open ports and the nmap-service-probes databases to query services to confirm the service running on a port and provide the version of the service running. This allows exploits to better or properly chosen for use since different versions and patches are susceptible to different things.
nmap -sV 10.30.50.70
-
Maimon scan
A maimon scan is a FIN/ACK probe. Named after the discoverer, it is meant to determine open and closed ports on BSD derived systems. Other systems will generate a RST packet regardless of the port’s state. No response indicates either open or filtered, RST closed, and ICMP unreachable error as filtered.
nmap -sM 10.90.20.80
-
Protocol Ping
A protocol ping sends IP packets with the specified protocol number or ICMP, IGMP, and IP-inIP by default. When sending only ICMP, IGMP, TCP, and UDP send with properly configured headers. This scan looks for active protocols on the target. Not currently working
nmap -PO 43.76.12.93
-
ICMP echo discovery probe
An ICMP echo ping uses the ping program to send an echo request(8) expecting an echo reply(0) back from available hosts. many devices are set to either drop or reject pings now making this an ineffective scan against properly defended networks. This is expected to be used mainly by system admins against their internal network.
nmap -PE 88.55.22.77
-
Timestamp Discovery Probe
A timestamp probe functions in the same fashion and with the same issues and a ICMP echo discovery probe. However, it uses a ICMP code 14(timestamp reply) instead.
nmap -PP 10.9.8.7
-
Netmask Request Discovery Probe
A netmask request probe uses the same basis as both the ICMP echo discovery probe and the timestamp discovery probe. For this scan, however, it uses the ICMP code 18(address mask reply) instead.
nmap -PM -Pn 5.3.7.9
-
TCP SYN Discovery Ping
A syn/ack discovery ping sends an empty TCP packet with only the SYN flag set. When sent this scan expects a RST packet if the port is closed or a SYN/ACK if the port is open. By default it uses only port 80 and is designed to work only for privileged users on Unix boxes. The scan automatically uses a workaround if the user is not privileged.Returns improper results
nmap -PS21-50 55.66.77.22
-
TCP ACK Discovery Ping
A TCP discovery ping works like the SYN Discovery ping but sets the ACK flag instead of the SYN flag. Both are offered to better allow a user access around or through a firewall.Only works on the same network
nmap -PA21-50 1.9.2.8 hping3 -c 1 -V -p 80 -s 5050 -A 10.9.2.8 (TCP ACK Scan)
-
UDP Discovery Ping
A UDP Discovery scan uses the same idea as both the SYN Discovery ping and the ACK Discovery ping. The difference here is that instead of a TCP packet it uses a UDP packet. Packets are empty except for a few ports(53 and 161). ICMP unreachable messages indicate a closed port, any other ICMP message or no response indicates a down/unreachable host, open ports also will drop responses if there is no payload. The lack of true responses makes this an unreliable scan, but it is able to get around firewalls designed for TCP. Does not return proper response
nmap -PU21-50 45.60.75.90
-
SCTP INIT Scan
A SCTP INIT scan has characteristics of both TCP and UDP with other features as well. This is the SCTP version of the TCP SYN scan and is able to get through most firewalls. It is considered fairly stealthy and gives reliable open, closed, and filtered results. An INIT-ACK shows as open, no response shows as filtered, and ABORT shows as closed.
nmap -sY 17.34.51.68
-
Additional "nmap" Options
-
-n disables name resolution
-
-R resolves names to IP addresses
-
-iR choose random targets
-
-p port ranges
-
-F Fast mode
-
-v verbosity level
-
-d debugging level
-
-6 IPv6 scanning
-
-A OS detection, version detection, script scanning, and traceroute
-
Active External Network Reconnaissance: Scans with Netcat
| It is important to ensure you identify what version of netcat you have installed, this will let you know what options you can and cannot use! |
nc [OPTIONS] [TARGET IP] [TARGET PORT] nc -h (Help Menu) man nc (Man Pages)
-z : Port scanning mode i.e. zero I/O mode.
-v : Be verbose [use twice -vv to be more verbose].
-n : Use numeric-only IP addresses i.e. do not use DNS to resolve ip addresses.
-w 1 : Set time out value to 1.
Example Scan syntax’s will look similar to this:
nc -zv [TARGET IP} 443 nc -zv [TARGET IP} 80 nc -zv [TARGET IP} 22 nc -zv [TARGET IP} 21 nc -zv [TARGET IP} smtp nc -zvn [TARGET IP} ftp ## really fast scanner with 1 timeout value ## netcat -v -z -n -w 1 [TARGET IP} 1-1023
Netcat Banners
echo “” | nc -zv -wl [host] [port range] – obtain the TCP banners for a range of ports
Netcat Web COntent
printf “GET / HTTP/1.0\r\n\r\n” | nc google.com 80 - how to obtain the HTML content from Google’s homepage:
Netcat TCP port Scanner
#!/bin/bash
echo "Enter network address (e.g. 192.168.0): "
read net
echo "Enter starting host range (e.g. 1): "
read start
echo "Enter ending host range (e.g. 254): "
read end
echo "Enter ports space-delimited (e.g. 21-23 80): "
read ports
for ((i=$start; $i<=$end; i++))
do
nc -nvzw1 $net.$i $ports 2>&1 | grep -E 'succ|open'
done
# (-v) running verbosely (-v on Linux, -vv on Windows),
# (-n) not resolving names. numeric only IP(no D.S)
# (-z) without sending any data. zero-I/O mode(used for scanning)
#(-w1) waiting no more than 1second for a connection to occur
# (2>&1) redirect STDERR to STDOUT. Results of scan are errors and need to redirect to output to grep
# (-E) Interpret PATTERN as an extended regular expression
# ( | grep open) for Debian to display only open connections
# ( | grep succeeded) for Ubuntu to display only the open connections
References:
Active External Network Reconnaissance: Other One Liner scanners
Scan 1 system for a range of ports using Netcat:
for i in {20..65535}; do nc -nzvw1 192.168.65.20 $i 2>&1 & done | grep -E 'succ|open$'
Scan 1 system for a range of ports using /DEV/TCP:
for p in {1..1023}; do(echo >/dev/tcp/10.0.0.104/$p) >/dev/null 2>&1 && echo "$p open"; done
Scan a range of IPs for specific ports using Netcat:
for i in {1..254}; do nc -nvzw1 192.168.65.$i 20-23 80 2>&1 & done | grep -E 'succ|open'
Ping scan a range of IPs:
for i in {1..254}; do (ping -c 1 192.168.65.$i | grep "bytes from" &) ; done
Network owners must understand what information can be gleaned from their network traffic and have a full understanding of their network footprint. Information can be gathered from a target passively by eavesdropping on a target using tools such as Wireshark, tcpdump, and tshark. However, information about a network and devices can be easily gained from a machine access has been granted to or has been compromised.
Passive Internal Network Reconnaissance: Information Gathering on Hosts
What are some ways to gather useful network information through commands issued on a local host?
-
IP Address
Windows: ipconfig Linux: ifconfig Linux: ip addr
-
System DNS
Displays all current TCP/IP network configuration values and refreshes Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) settings. Used without parameters, ipconfig displays Internet Protocol version 4 (IPv4) and IPv6 addresses, subnet mask, and default gateway for all adapters. Additional provided valuable:
/displaydns
Displays the contents of the DNS client resolver cache, which includes both entries preloaded from the local Hosts file and any recently obtained resource records for name queries resolved by the computer. The DNS Client service uses this information to resolve frequently queried names quickly, before querying its configured DNS servers.
/all
Displays the full TCP/IP configuration for all adapters. Adapters can represent physical interfaces, such as installed network adapters, or logical interfaces, such as dial-up connections.
-
ARP (Address Resolution Protocol)
* /-a Displays current ARP cache tables for all interfaces.
-
Services File
The services file provides a list of well-known port numbers mapped to each commonly associated service and any optional aliases that the service may use. Each OS maintains this file, which follows a simple structure.
-
services file format:
<service> <port>/<protocol> <aliases> #Comments
Example:
http 80/tcp www www-http #World Wide Web
In this example, TCP port 80 is associated with the http service and two optional aliases, www and www-http, are given. The services file is located most commonly in the /etc/ directory and the table below shows common locations by OS.
Protocol & Port Common Service TCP 21 FTP TCP 22 Secure Shell (SSH) TCP 23 Telnet TCP 25 SMTP (email) TCP/UDP 53 DNS UDP 67/68 DHCP TCP 80 HTTP TCP 110 POP3 (email) UDP 123 Network Time Protocol (NTP) TCP 443 HTTPS TCP 445 Server Message Block (SMB) (File Sharing) UDP 514 Syslog
-
OS Location
Windows: %SystemRoot%\system32\drivers\etc\services Linux/Unix: /etc/services
Keep in mind that the port mappings are just a simple translation from port to service name. It is possible for an HTTP server to be listening on port 23, but the OS which is using the services file would still list telnet.
Passive Internal Network Reconnaissance: Traffic Sniffing
-
Sniffing network traffic is one of the most useful passive techniques, but possibly the most involved. Even without a SPAN port, useful traffic is broadcast on a switched network. ARP/NDP and DHCP requests tell about hosts; CDP and STP inform about infrastructure devices; and the Server Message Block (SMB) Protocol is always seeking peers. If the point of presence is a server, other hosts send traffic to it, then use TTLs and ephemeral ports to guess what type of OS is generating the traffic. Passive OS fingerprinting gives a much more precise guess. Remember, TTLs, MAC addresses, and IP addresses can tell if the sending system is on the local network or has to be routed.
-
Capturing raw signals from the wire is an easy way to learn about a network and how devices and applications communicate. Hardware-based sniffers are best for capturing raw signals from the wire, though they range in price and accessibility. Software-based sniffers rely on the NIC of the host system to relay traffic through the OS and usually cannot see all signals on the wire, such as the preamble and a frame’s CRC, limiting their use in some situations. Another limiting factor of software sniffers is the operating mode of the NIC, of which two exist:
-
Non-promiscuous — default mode for most NICs. Only passes traffic destined for its MAC address, its multicast groups, or broadcast.
-
Promiscuous — the NIC passes all signals to the OS. Most Unix-based systems support promiscuous mode natively; Windows requires additional drivers to enable promiscuous mode, such as WinPcap. Most software sniffers use the standard BPF syntax. The most common output file format is the standard .pcap file (packet capture).
-
tcpdump — A command-line tool native to most Linux systems and has been ported to Windows and many Berkeley Software Distribution (BSD)-based systems.
-
Wireshark — A graphical user interface (GUI)-based tool with its own display filter syntax. Available on Windows and most Linux distributions.
-
Map a network through correlation of relevant network artifacts gathered through Reconnaissance and analysis
-
Basic net mapping from provided information i.e. papers and configurations was previously done in JCAC/CBTC.
-
You will need to know how to accomplish the same end task(creating an accurate and complete network map) with different starting materials i.e. provided traffic and the provided network.
-
The concepts below should be briefly reviewed to facilitate the best possible outcomes for the rest of the course activities and exercises.
-
Different units and missions may require accompanying documents to your network map(s) and network map standards may vary between units in addition to whether you are offensive or defensive.
Pictures will be provided to demonstrate the differences between offensive and defensive maps.
Draw.io Demo
Offensive Mapping:
-
Diagram devices:
-
Depending on the data available it may not be possible to see all devices on the network for a variety of reasons such as the layer that a device functions at, or where a device is located in a network.
-
Routers
-
Hosts
-
Servers - Knowing where and what servers are can provide additional context and information for future planning.
-
Firewalls
-
Clouds - This pertains to both cloud services utilized and elements outside of the target network.
-
Switches - This type of device is often not seen offensively due to the layers that they function at.
-

-
Types of lines:
-
Solid - Direct connection between devices
-
Dashed - Devices are able to talk but it has not been confirmed that they are directly connected i.e. there is a chance of a device between them.
-
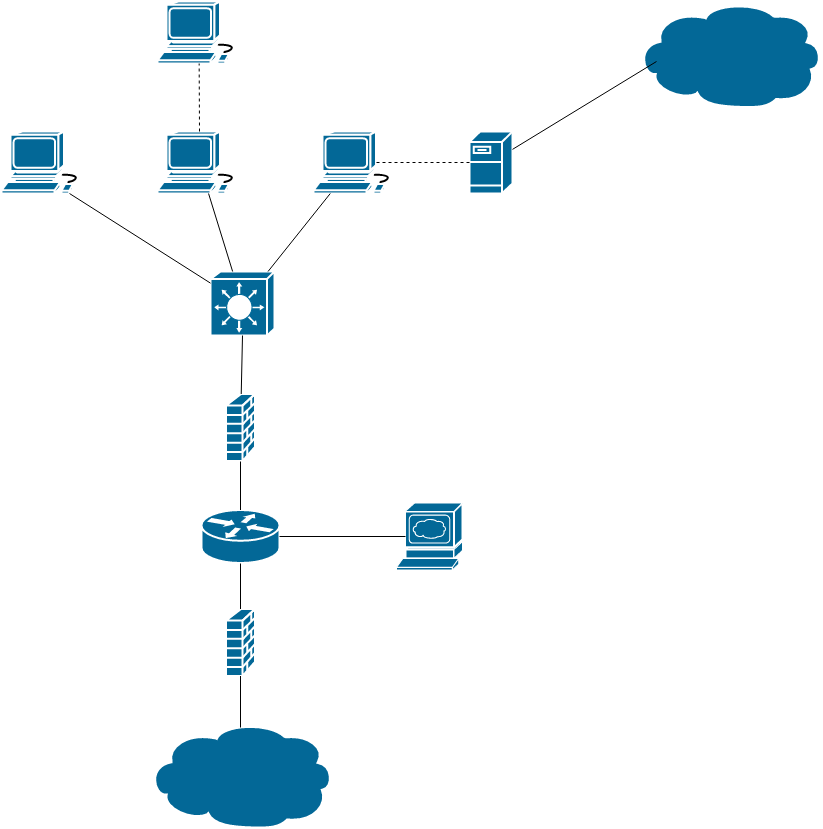
-
Additional Written Information: This is information that should accompany devices and additional groupings
-
Device names - Naming schema allows you to confirm what machine you are on and often tells you how many devices/ what unidentified devices may be called.
-
Versions/patches - This will help identify security features, functions, and vulnerabilities available.
-
Credentials
-
Ports/Services
-
-
Device Coloring: This is currently only done offensively to determine target and credential viability.
-
Red - Non viable target
-
Yellow - Possible target; non verified credentials or possible exploitable vulnerability
-
Green - Valid target with verified credentials or exploitable vulnerability
-

-
Additional Groupings: These are additional information and bounding areas that should also be placed on your network map but are not devices/ additional information for devices.
-
Routing Protocols
-
VLANS
-
NAT boundaries
-
Tunnels
-
